Single Sign-On (SSO)
Single Sign-On is set on an organizational level in , allowing users in that organization to log into the with their email address that authenticates against 3rd party identity providers (IDPs). This makes it easy for users to sign into the app with the same account (domains) used to access company systems.
SSO is only applicable when signing in on the . To log in to (manage.jigx.com) the organization OWNER and ADMIN must use their accounts.

Single Sign-On requires domains to be set up and associated with an organization, to view your organization's domains, see Advanced Settings in . The following scenarios are supported.
- One or more domains can be associated with a single organization
- A domain can be associated with multiple organizations
- Use a wildcard (*) in the OAuth Configurations to reference multiple unknown domains. The OAuth configuration will be used by every account, regardless of the domain.
supports the following 3rd party identity providers:
- Graph
- Okta
- OpenID
- Auth0
To enable the SSO configuration, at least one OAuth configuration is required. To configure OAuth, see OAuth Configurations
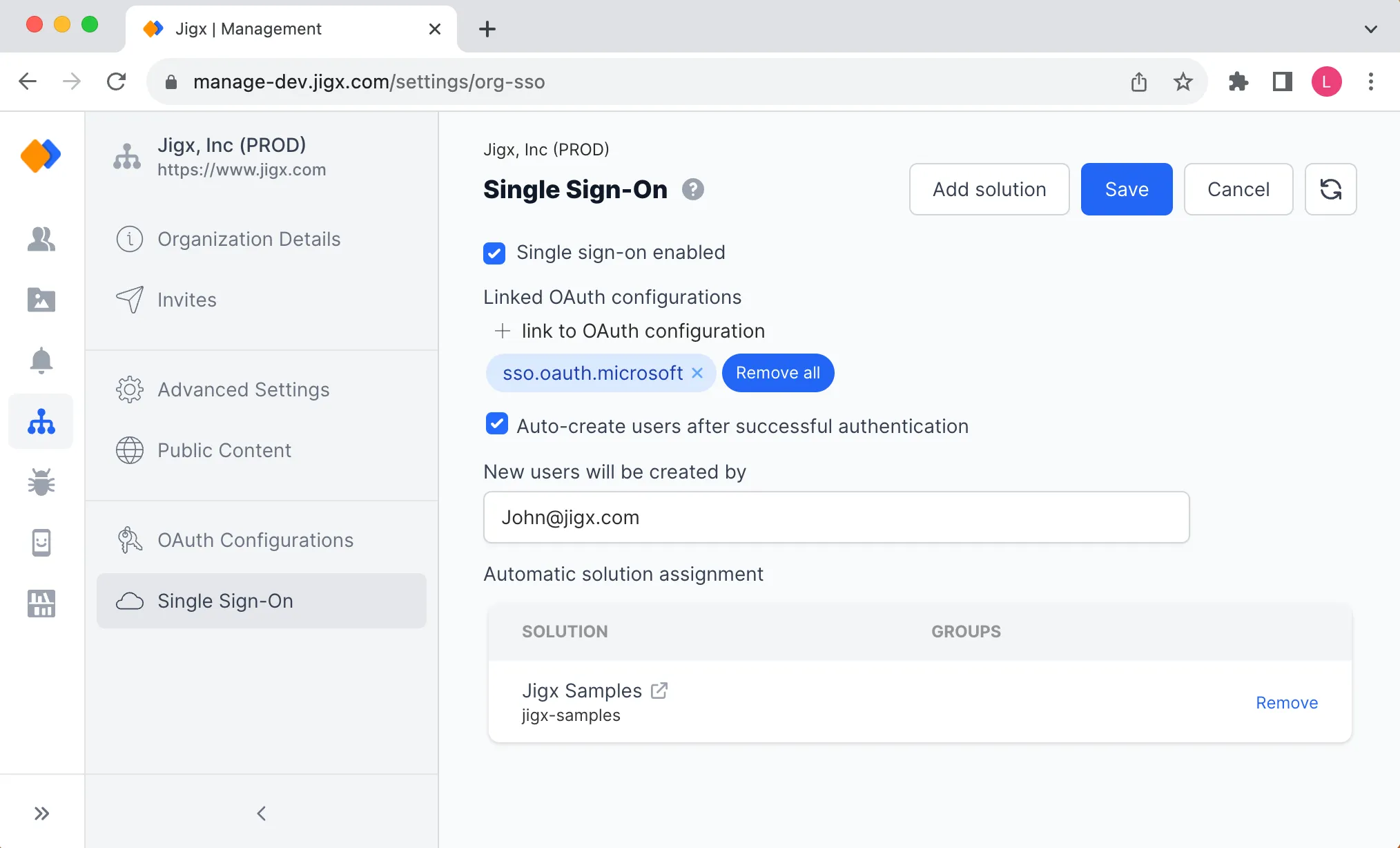
The table below describes the combinations possible when enabiling SSO.
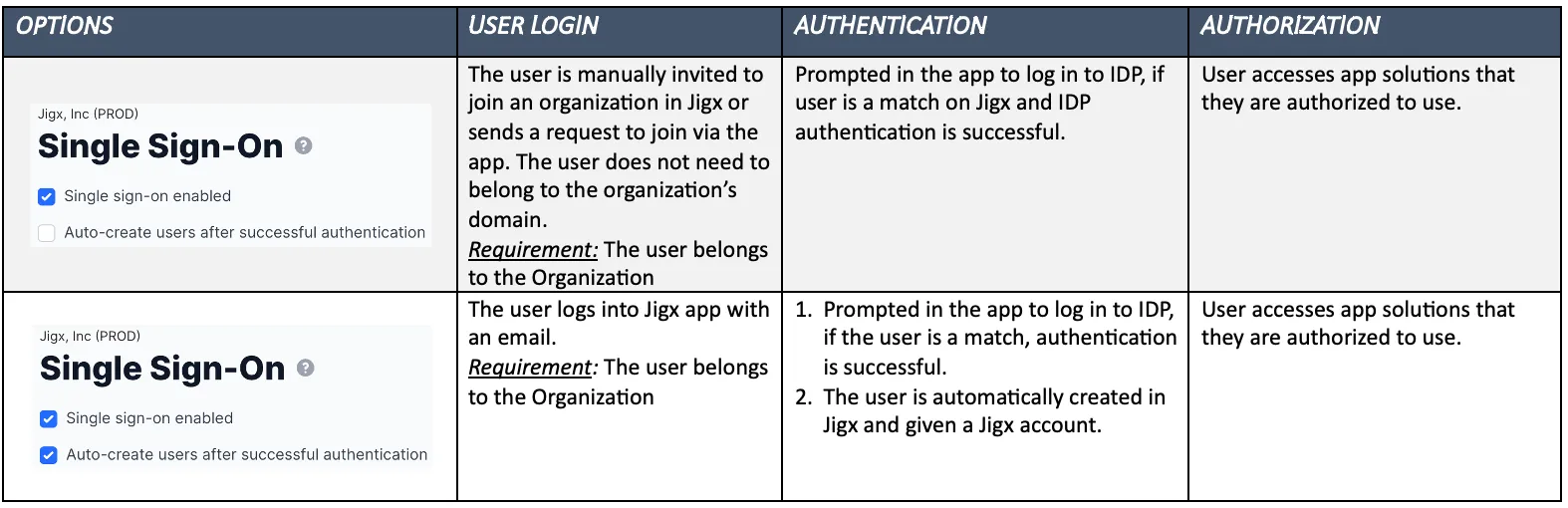
- In under the Organization icon, select the Single Sign-On option. You require ADMIN or OWNER permissions to see and access the organization settings.
- Select the Single Sign-On enabled checkbox. The configuration options show.
- Required - Click on + link to OAuth configuration to open the Choose OAuth configurations for SSO panel on the right. Select the checkboxes next to the available OAuth configurations that you want to use with SSO. If there are no available OAuth configurations in the pane go to OAuth Configurations to set one up.
- Selecting the Auto-create users after successful authentication checkbox, creates new users that sign into the with the organization's email address as a user after authenticating the user against the 3rd party identity provider.
- The users are automatically created with User rights (ability to use solutions on the app) in .
- For to automatically create these users in an organization an email address belonging to an existing user with Admin or Owner rights must be added to the New users will be created by field, think of it as the organization's admin creating the users. By default the user who enables the Auto create users after successul authentication checkbox email address is shown in this field.
- When a user joins an organization they need to sign in to the to be auto created in .
- If the checkbox is not selected, each user has to manually be created in before they can successfully sign in or they can request access via the app.
- If you want users to automatically be assigned to solutions, add the solutions to the Automatic solution assignment list. This ensures that all users that authenticate using SSO can automatically see and use the solutions as soon as they sign in. Users will also automatically be added to any existing groups in the assigned solution. Click the Add Solution button at the top right of the screen. Solutions assigned here will use the OAuth Configurations configured at an organizational level.
Once signed in to the app and the user is authenticated against the 3rd party indentity provider a Login Complete screen is shown and they can continue using the solutions in the app.


With SSO enabled when logging out of the you are prompted to log out of the 3rd party IDP account associated with the sign in. When logging back into the app you are prompted to sign back in to the 3rd Party IDP. This is useful if the same device is shared between colleagues.
- There is no system to keep and the IDPs in sync, meaning if new users join or an existing user leaves there is no automatic syncing between the IDP and . A manual task is needed to ensure the users are the same on both sides.
- Recommendation: Start with setting up the OAuth Configurations before enabling SSO. To enable the SSO configuration, at least one OAuth configuration is required. The save button will not be enabled if no OAuth is linked.
- Auto-provisioning users is an optional setting, but if enabled, the email address is required in the New users created by field, as well as a link to at least one solution.
- A minimum of one OAuth configuration is required for SSO to work.
- If multiple OAuth configurations are set to work with SSO, the user will be presented with a popup displaying the multiple SSO options. It is important to give the OAuth configuration a meaningful Title as this becomes the option name presented to the user on the mobile device at login.